Table of Contents
Introduction
Let’s not sugarcoat it—healthcare data security in 2025 is no joke. And when the stakes are this high, HITRUST compliance isn’t just “nice to have”—it’s the gold standard.
Imagine PCI, NIST, and HIPAA combined into a single, stringent, certified framework. That’s HITRUST certification in a nutshell.
Do you need evidence? In 2024, only 0.59% of HITRUST-certified organizations experienced incidents—leaving 99.41% completely breach-free, according to the 2025 Trust Report.
This guide? It’s your roadmap. We’ll break down what is HITRUST, how it stacks up against HIPAA, and exactly how to get HITRUST certified—without the overwhelm.
What is HITRUST Compliance?
HITRUST Overview:
HITRUST compliance refers to meeting the security and privacy standards defined by the Health Information Trust Alliance (HITRUST). Established in 2007, HITRUST developed the Common Security Framework (CSF), a comprehensive, certifiable framework that unifies key regulations like HIPAA, ISO, NIST, and GDPR into one standardized system.
Why HITRUST?

Because HIPAA, while important, left way too much up to interpretation. Its security rules were broad, often confusing, and hard to implement—especially for smaller organizations without a full-blown IT team.
That’s where HITRUST came in. It gave the industry a standardized, certifiable framework—one that made HIPAA’s goals actually achievable.
Though HITRUST began in healthcare, its use now spans industries like finance, tech, and retail. Think finance, tech, retail—any industry that takes data protection seriously.
So, why HITRUST? Because it translates messy healthcare compliance chaos into one clear, trusted path to managing information risk.
Learn about healthcare compliances, explore our blog: The Ultimate Guide to Healthcare Compliance for Medical Practices
Who Should Care About HITRUST Certification and When?
Anyone handling sensitive health information should care about HITRUST certification, whether it’s a busy solo doctor, a large hospital chain, or even a tech vendor working with medical data.
HITRUST isn’t just for the “big players”; it’s a practical seal of trust for companies of any size that manage, transmit, or process PII & PHI. If protecting data, building patient or partner confidence, and simplifying compliance are priorities, the right time to consider HITRUST is whenever PHI enters your workflow.
Early adoption sets a foundation for security and future growth, while waiting can risk gaps and missed opportunities to stand out in a crowded healthcare market.
Understanding the HITRUST CSF
The HITRUST CSF is a unified, risk-based framework that brings together multiple security and privacy standards into one streamlined system. It simplifies compliance by eliminating overlaps, aligning regulatory and industry requirements, and adapting controls to an organization’s specific risk profile.
Continuously updated to reflect emerging threats and evolving best practices, the HITRUST CSF empowers organizations to build scalable, resilient, and future-ready security programs.
IIn simple words: simple words: simple words: At the core of HITRUST compliance is the Common Security Framework (CSF)—your shortcut through today’s chaotic security landscape.
Several standards, including HIPAA, NIST, ISO, PCI, and others, are combined into a single, coherent framework by the HITRUST CSF. Instead of juggling overlapping rules, you get a single roadmap to follow.
Here’s the real advantage: the CSF can be officially certified. CSF certified means you can prove your compliance to partners and regulators with confidence—not just policies on paper.
Less confusion. More consistency. And big efficiency gains.
With HITRUST CSF, you’re not just meeting security requirements—you’re simplifying them. And in a world where trust is currency, that’s a serious edge.
HITRUST Framework Structure and Control Domains
TL; DR:
HITRUST Framework & Control Domains
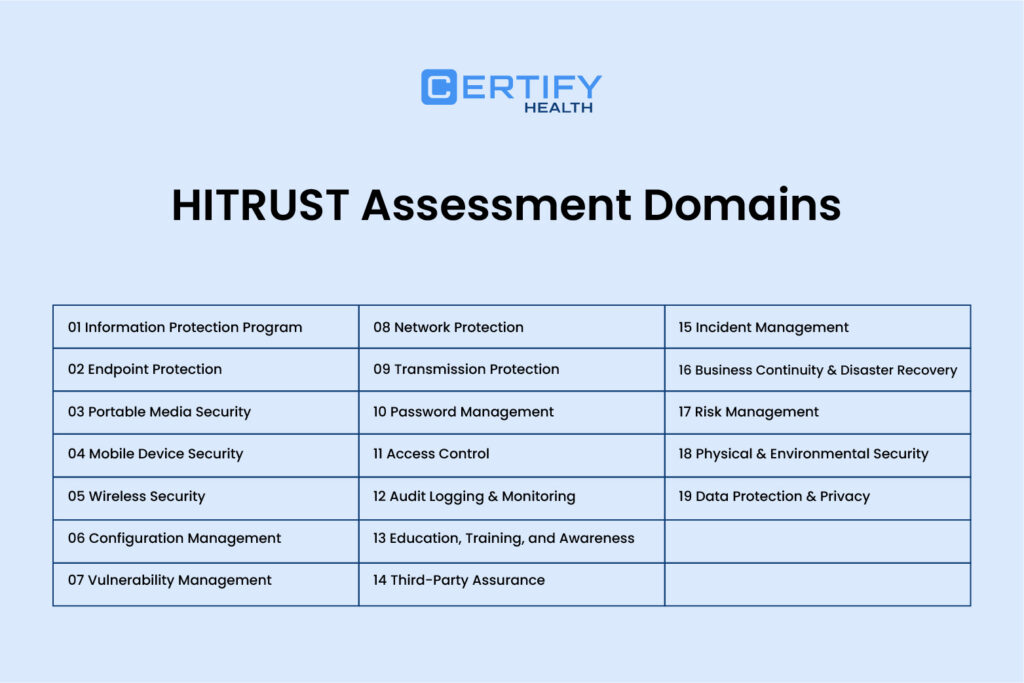
- HITRUST CSF includes 19 control domains, each targeting a core area of information security.
First 5 domains (foundation):
- Information Protection Program
- Endpoint Protection
- Portable Media Security
- Mobile Device Security
- Wireless Security
Next 5 domains (technical controls):
- Configuration Management
- Vulnerability Management
- Network Protection
- Transmission Protection
- Password Management
Final 9 domains (holistic controls):
- Access Control
- Audit & Monitoring
- Education & Training
- Incident Management
- Business Continuity & Disaster Recovery
- Risk Management
- Physical Environment & Safety
- Data Protection & Privacy
Why It Matters:
HITRUST unifies multiple frameworks (like HIPAA, NIST, GDPR) into one structure—streamlining compliance and boosting trust.
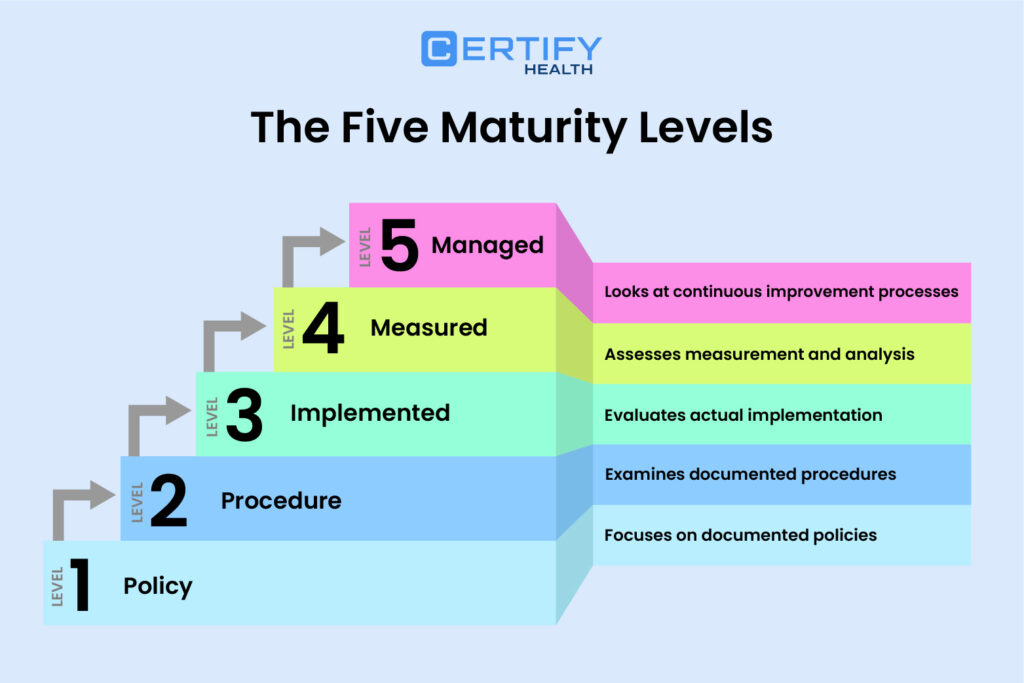
HITRUST Maturity Levels (5):
- Policy – Is it documented?
- Procedure – Is there a clear process?
- Implemented – Is it actually done?
- Measured – Are results tracked?
- Managed – Is there continuous improvement?
Assessments:
- i1 → Evaluates “Implemented” level only.
- r2 → Evaluates “Policy,” “Procedure,” and “Implemented,” with optional deeper levels.
In essence: HITRUST doesn’t just measure compliance—it measures how mature and effective your security really is.
Control Specifications: The 19 Control Domains
The HITRUST CSF is built around 19 distinct control domains—each one laser-focused on a specific area of information security. And if you’re serious about HITRUST compliance, knowing these domains isn’t optional—it’s essential.
The first five? That’s your foundation.
You start with the Information Protection Program domain. It’s all about building your security game plan—policies, procedures, standards, and yes, even how you handle risk assessments and respond to incidents. Think of this as the “mission control” of your data protection strategy.
From there, it gets tactical.
- Endpoint Protection: desktops, laptops, servers—you name it.
- Portable Media Security: we’re talking about those sneaky USB drives and external storage devices.
- Mobile Device Security: because these days remote work is highly common.
- Wireless Security: your shield against unauthorized network access.
Still with me? Good—because here’s the kicker:
There are 14 more domains to go. Surprised? Most are. But that’s where the depth of the Common Security Framework (CSF) really shows.
The next set (domains 6–10) handles the more technical side of the house:
- Configuration Management
- Vulnerability Management
- Network Protection
- Transmission Protection
- Password Management
These domains focus on proactive defenses—keeping threats out before they even knock.
Now pause for a second. Ever thought, “Wow, HITRUST covers everything”?
You’re not wrong.
The final set of domains takes a holistic view:
- Access Control
- Audit Logging & Monitoring
- Education & Training
- Incident Management
- Business Continuity & Disaster Recovery
- Risk Management
- Physical Environment & Safety
- Data Protection & Privacy
Every one of these is a building block in reducing risk, increasing trust and reputation, and simplifying vendor management.
So, when someone asks “Why HITRUST?”, this right here is your answer. It’s not just about meeting one requirement—it’s about aligning with multiple compliance standards through a single, unified approach. That’s the power of being CSF certified.
The Five Maturity Levels
Here’s where HITRUST takes things up a notch—it doesn’t just check off whether your security controls exist. Nope, that would be too easy.
Instead, it asks a tougher question: How well are those hitrust controls actually working?
Enter the five HITRUST levels. These aren’t just technical jargon—they’re a way to measure the depth and reliability of every control you’ve implemented. From simply having something in place… to consistently optimizing it, these HITRUST levels help paint a clear picture of your security posture.
HITRUST Levels:
- Level 1: Policy – Focuses on documented policies
- Level 2: Procedure – Examines documented procedures
- Level 3: Implemented – Evaluates actual implementation
- Level 4: Measured – Assesses measurement and analysis
- Level 5: Managed – Looks at continuous improvement processes
All the maturity levels or a few of them may be assessed based on the kind of HITRUST assessment. For instance, HITRUST i1 Assessments focus solely on evaluating the Implemented level, whereas r2 Assessments automatically assess the Policy, Procedure, and Implemented levels, with the flexibility to include Measured and Managed levels if needed.
This maturity model gives businesses a clear way to get better. Rather than a binary “compliant/non-compliant” determination, HITRUST offers a nuanced view of security posture maturity that supports ongoing development.
HITRUST vs HIPAA: Understanding the Relationship
TL; DR:
HIPAA vs HITRUST
HIPAA = The Law. It’s mandatory and defines what patient data must be protected. But it doesn’t tell you how to do it.
HITRUST = The Framework. It’s voluntary but highly structured, combining HIPAA, NIST, ISO, and PCI into one unified set of security controls.
Key Difference:
- HIPAA relies on self-assessment — you claim compliance.
- HITRUST demands independent validation — you prove compliance through audits and evidence.
This one trips up a lot of people. So, let’s clear the air.
HIPAA compliance is federal law. It’s mandatory. If you’re a healthcare provider or a business associate, you must follow it. But here’s the catch: HIPAA tells you what you need to protect… it doesn’t really tell you how to do it.
Now here’s where HITRUST compliance comes in.
HITRUST isn’t the law—it’s a voluntary framework built by healthcare and security experts. And while it does include HIPAA requirements, it goes way beyond that. It pulls in standards from NIST, ISO, PCI, CMMC, and more.
Think of it like this:
HIPAA compliance = the “what” of security
HITRUST compliance = the “how”
Here’s the magic: If you’re HITRUST certified, you’re already meeting HIPAA—and then some. It’s a smarter, more thorough way to prove your data security program is actually working.
Assessment and Validation Differences
HIPAA compliance is mostly based on the honor system. No, seriously. It’s primarily a self-assessment process—meaning, organizations are responsible for determining if they’re compliant. The federal government does not officially issue HIPAA certifications. You’re basically saying, “Yep, we’ve got it under control,” and hoping that holds up if there’s ever an audit.
HITRUST certification? Totally different game.
Instead of just checking your own boxes, HITRUST takes you through a rigorous, multi-stage process that includes third-party assessors, complete validation, and different levels of assurance. You don’t just claim compliance—you prove it. With documentation, evidence, and independent review.
And this isn’t just red tape.
That independent HITRUST certification is powerful. It tells business partners, regulators, and even patients that you’ve gone the extra mile—and that your security posture is solid. In fact, many organizations now expect or require it.
So, let’s sum it up:
HITRUST vs HIPAA isn’t a competition. It’s a complementary relationship.
HIPAA compliance gives you the legal baseline.
HITRUST certification gives you the blueprint (and validation) to actually meet—and often exceed—that baseline.
One tells you what to do. The other shows you how—and helps prove you did it.
Pro tip: Understanding HIPAA is one thing—applying it to real workflows like patient intake is where things get tricky. So, you may also want to check out – complete guide on HIPAA-compliant patient intake.
HITRUST Certification Levels and Process
Understanding HITRUST Assessment Types
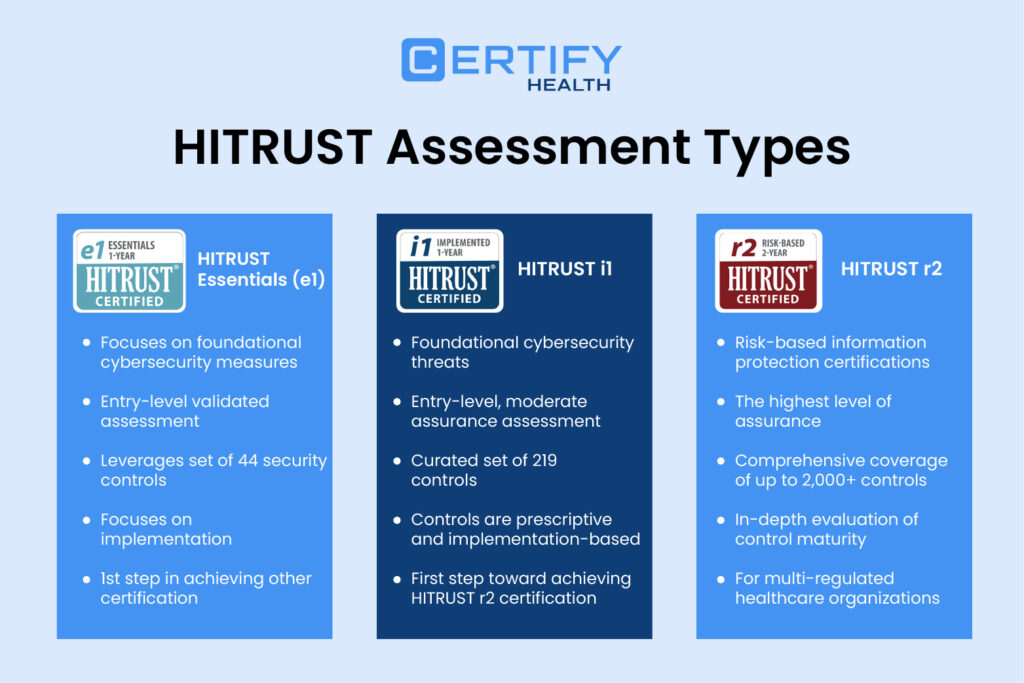
The three main types of assessments include:
- e1 (Essential): Focuses on basic hygiene controls for smaller organizations or those new to the framework
- i1 (Implemented): It includes intermediate controls with wider coverage
- r2 (Risk-based): The most rigorous and comprehensive assessment, typically pursued by larger organizations or those with complex security requirements
A different degree of assurance is provided by each HITRUST self-assessment, with the r2 giving highest degree of assurance. The choice between these options depends on factors such as organizational size, complexity, and specific compliance requirements.
But here’s something important to understand: regardless of which assessment type you choose, each requires thorough preparation and evidence submission.
The Path to Certification

So, how do you actually get HITRUST certified? Here are the steps:
1. Define scope
Map everything out before you do anything else. Identify every system, process, and location where protected health information is stored, transmitted, or created. This step is important –get this wrong, and the rest wobbles.
2. Create a MyCSF account
Next, register on HITRUST’s MyCSF platform. It’s your mission control. All tracking, documenting, and assessment activities flow through MyCSF—your best friend throughout this journey.
3. Conduct a gap analysis
Here’s where reality hits. Check to see if your current security postures comply with HITRUST. A detailed gap analysis tells you what you’re missing and helps prioritize the fixes before getting into the heavy lifting.
4. Remediate identified gaps
Time to roll up your sleeves. Implement the procedures, policies, or technical controls required to close the gaps found.
5. Engage a HITRUST certified assessor
Now bring in the experts. A HITRUST certified assessor will now start official validation assessment. Their job? Ensure you’re not just checking boxes but truly aligning with HITRUST’s stringent framework.
6. Submit evidence and complete validation
This is the moment of truth. You’ll provide detailed documentation, control implementation evidence, and walkthroughs for the assessor to verify. Providing complete validation of each step is essential to establish credibility and demonstrate genuine compliance.
7. Receive certification
Congrats! Once all of the steps are done, you get your HITRUST certification, that will stay valid till two years. But the work doesn’t stop there.
8. Maintain ongoing compliance
HITRUST doesn’t do “set it and forget it.” Annual self-assessments and interim reviews help ensure you continue meeting evolving HITRUST requirements. This ongoing diligence is what separates truly secure organizations from the rest.
Here Are Top 5 HITRUST Benefits
TL; DR:
Top 5 HITRUST Benefits
- Streamlined Compliance: One assessment covers HIPAA, PCI, ISO—less redundancy, more efficiency.
- Risk Reduction: Strong controls cut breach risks and improve response.
- Trust & Reputation: Proves data security commitment and builds confidence.
- Cost Efficiency: Fewer audits, lower penalties, long-term savings.
- Vendor Management: Aligns vendor security, reducing third-party risks.
Let’s talk about HITRUST benefits:
Streamlined Compliance
With HITRUST compliance, you can ditch the redundancy!
It is all because of HITRUST “assess once, report many” approach, where a single assessment covers different types of regulations such as HIPAA, PCI DSS, and ISO 27001.
This not only saves you time but cuts down on the headache of managing different compliance requirements. Streamlined compliance benefits your practice by ensuring fewer hassles and more time to scale your business.
Risk Reduction
Here’s the thing: when you’re HITRUST-certified, you’re locking down your security like a vault. The framework’s 19 control domains cover everything—from access control to business continuity.
It’s a comprehensive approach that reduces risk and ensures that every angle is covered. And let’s be real—HITRUST-certified organizations experience fewer breaches. Why? Because you’re proactively addressing security at every level.
But what about if a breach does happen? With HITRUST compliance, you’ve got incident management and data encryption in place to mitigate damage and recover faster. Pretty smart, right?
Trust and Reputation
What does your reputation mean to you? Because with HITRUST certification, you’re not just ticking off security standards. You’re building trust and reputation.
Patients, partners, and payers are more worried about the safety of their sensitive information. But when you’re HITRUST-certified, you’re sending a loud and clear message: data security and compliance is your top priority.
That trust doesn’t just help you win clients—it keeps them coming back. Trust isn’t just earned; it’s demonstrated. And HITRUST certification does exactly that.
Cost Efficiency
HITRUST compliance doesn’t just save you time; it saves you money. You’re streamlining compliance efforts, cutting down on audit expenses, and simplifying compliance management.
And think about this—by reducing the risk of fines or penalties from non-compliance, you’re cutting long-term costs too. All that effort? Totally worth it in the long run. HITRUST compliance helps achieve cost efficiency and stay secure.
Vendor Management
We all know third-party risks are a big deal. Massive headaches could result from a single vendor leak. But with HITRUST compliance, you’re not leaving things to chance.
You’re setting clear security controls for your vendors, ensuring they meet the same high standards as you do. Think of it as building a secure fence around your entire supply chain.
By ensuring your vendors are on the same page, you’re protecting your organization from potential breaches and making life easier when it comes to managing third-party risks. So yeah, it’s a win-win.
Pro Tip: Healthcare practices who want to experience these benefits must look for a HITRUST-certified solutions like CERTIFY Health. It doesn’t just check a compliance box—it benefits you by simplifying your entire workflow. From digital intake to billing, you’re reducing overhead and risk with one trusted solution.
Making HITRUST Sustainable
Achieving initial certification is just the beginning. Maintaining HITRUST compliance calls for constant efforts and resources.
Implement continuous monitoring practices to ensure controls remain effective between assessments. Automated tools can help track key security metrics and identify potential issues before they become significant problems.
Develop a robust documentation management system. HITRUST requires extensive evidence, and maintaining organized, accessible documentation significantly reduces the burden of annual assessments and recertification.
Create a change management procedure that takes security concerns into account. New systems, workflows, or organizational changes may affect your HITRUST compliance status. Evaluating these changes through a security lens helps maintain continuous compliance.
Finally, foster a security-conscious culture throughout your organization. IT is not the only department responsible for HITRUST compliance; all employees must be aware of it and take part. Regular training and communication about security practices help embed security awareness into your organizational DNA.
Remember that HITRUST compliance is a journey, not a destination. The framework evolves as threats and regulations change, requiring ongoing attention to maintain your security posture. The latest HITRUST CSF version (v11.3.0 released in April 2024) includes updates reflecting current threats and regulatory requirements, highlighting the importance of staying current with framework changes.
Conclusion: The Value of HITRUST in Today's Healthcare Landscape
Think HITRUST is just another checkbox? Think again. It’s your frontline defense in a world of rising cyberattacks and tightening regulations.
HITRUST isn’t just about passing audits—it’s about fewer breaches, lower risk, and stronger patient trust. Certified organizations report fewer security incidents.
Start small with an e1 or i1 assessment, do a quick gap check, and get your team on board.
Because in healthcare, it’s not if but when data gets targeted. And HITRUST? That’s how you maintain your readiness, security, and trust in this way.