Table of Contents
Security Risks in Digital Patient Intake: Why Data Protection Begins at the Front Desk
Security risks in digital patient intake directly translate to data breaches and financial losses in the healthcare sector.
Healthcare remains the single most exposed sector in the U.S. when it comes to digital security.
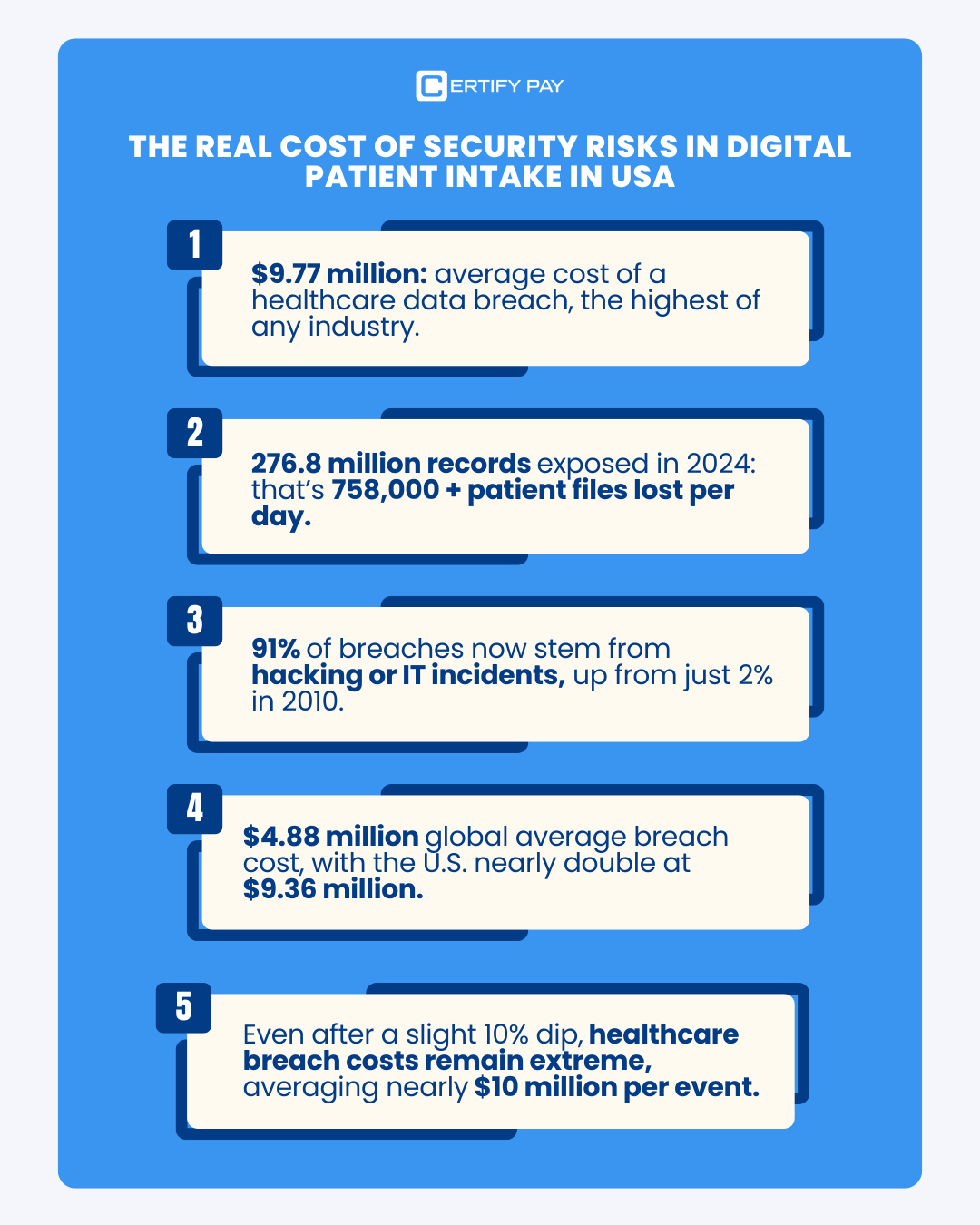
And here’s the kicker: the average breach now hits $7.42 million in losses and drags on for about 9 months before it’s even fully identified and contained, according to IBM’s latest 2025 Cost of a Data Breach Report.
Every day, patients trust their providers with deeply personal data (medical histories, demographic details, insurance credentials) and expect it to remain safe. That trust is sacred, and it demands absolute accountability from every healthcare organization handling patient information.
Yet, the numbers tell a worrying story.
In the U.S., 52% of healthcare staff admit to reusing passwords. That is a basic security lapse that continues to expose healthcare systems to ransomware, phishing, and unauthorized access. When something as critical as patient management systems relies on weak or shared credentials, it’s not a matter of if a breach will happen, but when.
This blog explores the top security risks in digital patient intake, backed by evidence-based data and strategic mitigation frameworks that healthcare leaders can implement today.
At the foundation of this effort lies HIPAA Security Compliance, the cornerstone of digital health protection in the U.S. The framework mandates security across three essential layers:
- Administrative safeguards: Policies, access controls, and staff training.
- Physical safeguards: Securing hardware and infrastructure.
- Technical safeguards: Encryption, authentication, and data access protocols.
Despite these requirements, human error remains the number one cause of data breaches in healthcare. Weak passwords, shared logins, and untrained staff have collectively cost the industry millions of dollars in losses, not to mention the erosion of patient trust and safety.
| Consequence | Description |
|---|---|
| Financial Cost | Healthcare has the highest average cost per compromised record of any industry, often due to regulatory fines (like HIPAA) and complex recovery efforts. |
| Operational Disruption | Attacks, especially ransomware, can shut down hospital networks, forcing operations to be diverted or postponed, directly impacting patient care. |
| Identity Theft | Stolen PHI is highly prized on the dark web for committing medical insurance fraud. |
| Reputational Damage | Loss of patient trust and damage to the provider's reputation. |
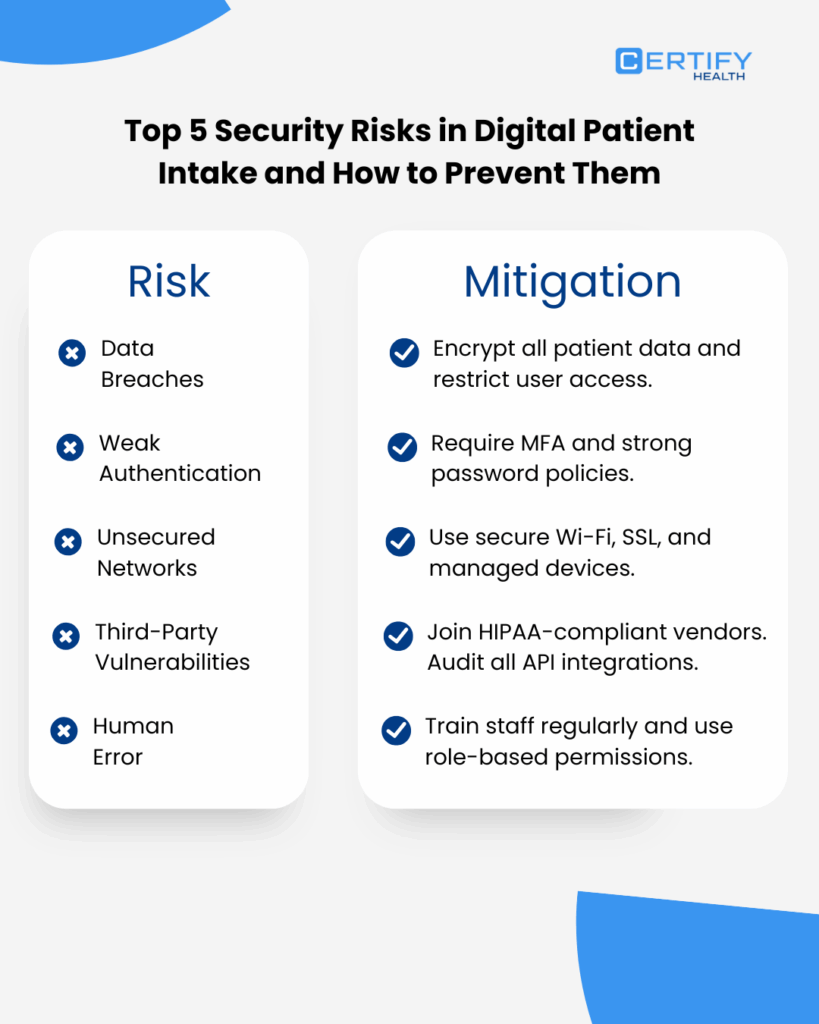
Protect Patient Intake Data: Top 5 Risks and the Mitigations
1. Ransomware Attacks on Patient Intake Systems
Ransomware is one of the most malicious cybersecurity threats in healthcare today. At its core, ransomware is a type of malware that infiltrates healthcare systems, encrypts patient records, and locks both patients and providers out of their data. Access is only restored after paying a ransom to the attackers.
In 2024, over 67% of healthcare organizations reported ransomware attacks, marking a staggering 60% increase from the year before. This rise underscores a sobering truth: digital patient intake systems are prime targets for cybercriminals seeking sensitive health data.
Did you know?
A single ransomware incident in 2024 exposed 190 million patient records after a breach in a third-party patient intake portal.
The attack not only compromised personal health data but also disrupted clinical operations nationwide.
The problem is compounded by outdated infrastructure. The surveyed healthcare providers still rely on legacy systems and 58% reported that ransomware infiltrations spread to connected medical devices, causing both operational and financial damage.
To stay ahead, healthcare organizations must modernize their IT architecture, implement robust incident response systems, and choose HIPAA-compliant, cybersecurity-ready digital intake platforms. The cost of prevention is minimal compared to the cost of recovery.
How to Mitigate Ransomware Attacks in Healthcare?
| 1. Automate and Test Backups Back up patient intake data automatically and verify recovery often. A tested backup separates continuity from crisis when ransomware strikes. |
| 2. Detect Threats in Real Time Deploy AI-driven monitoring to flag anomalies instantly. Real-time detection stops small intrusions before they become full-scale lockouts. |
| 3. Execute a Clear Incident Response Plan When seconds count, confusion kills response. Define roles, rehearse actions, and ensure your team moves fast and in sync. |
| 4. Segment Networks to Contain Damage Keep digital intake data on a separate, secured network. Isolation limits ransomware spread and shields critical patient information. |
2. Healthcare Data Breaches Due to Hacking and weak credentials
Despite rapid advancements in healthcare cybersecurity, 2024 saw one of the most alarming data theft spikes in recent times. Over 725 healthcare databases were breached, exposing thousands of sensitive patient health records.
The disturbing part? Nearly 35% of these attacks directly targeted digital patient intake accounts, where personal health data is often entered and stored.
In many cases, the breaches weren’t the result of sophisticated hacking tools, but of simple human negligence.
A recent Healthcare IT News report revealed that 73.6% of hospitals surveyed admitted to staff sharing passwords among peers and departments. Such behavior is not only a direct HIPAA violation, but also an open invitation for ransomware and unauthorized access.
How to mitigate Hacking of Hospital Systems?
| 1. Mandate Multi-Factor Authentication (MFA) Require MFA for every login. A stolen password means little when a second layer blocks the door. |
| 2. Eliminate Shared Credentials Ban password sharing. Use Single Sign-On (SSO) to simplify secure access and ensure accountability. |
| 3. Audit Third-Party Vendors Trust but verify. Audit vendors handling intake data for HIPAA compliance and cybersecurity rigor. |
| 4. Build a Culture of Awareness Technology can’t replace vigilance. Train every staff member to spot threats and act before damage is done. |
3. Phishing and Social Engineering Attacks
In healthcare, the most dangerous cyberattacks often don’t start with code; they start with trust.
Social engineering attacks exploit human psychology, manipulating people into taking unsafe actions like clicking a link or sharing credentials without realizing the consequences.
Phishing is the most common and damaging form of social engineering. Attackers pose as legitimate healthcare providers or trusted digital intake platforms, sending fake emails, text messages, or patient portal notifications that lure users into clicking malicious links. Once clicked, these links open the door to data theft, financial fraud, and system breaches.
Did you know?
In 2024, the U.S. healthcare sector lost $9.77 million to phishing attacks, which is more than any other sector.
That same year, 79 healthcare organizations reported breaches to the HHS Office for Civil Rights, exposing the medical histories of over 464,000 patients.
The problem is amplified by the urgency inherent in healthcare workflows. Staff and patients alike often click links that seem time-sensitive. For e.g., “View your next appointment” or “Confirm your medical form submission.” Combined with weak password practices and credential sharing, phishing becomes an open gateway to large-scale data breaches.
Phishing Attack Mitigation Strategies for Healthcare Staff
In healthcare, the inbox is often the weakest link. Strengthen it with technology, training, and authentication.
| 1. Deploy Advanced Email Filtering Use AI-powered filters to block or quarantine suspicious messages before they hit inboxes. One intercepted email can stop a costly mistake. |
| 2. Mandate Continuous Staff Training Run regular phishing simulations and awareness sessions. A well-trained employee can spot the bait before it’s clicked. |
| 3. Enforce Email Authentication Protocols Implement SPF, DKIM, and DMARC to validate senders and shut down spoofing before it reaches your network. |
4. Legacy Systems and Unpatched Software
In many hospitals, legacy systems or old technologies are retained because they still continue to run critical patient care operations. Similarly, unpatched software, which lacks the latest security updates, remains embedded deep within healthcare networks.
Together, these outdated systems form one of the biggest cybersecurity vulnerabilities in the healthcare industry.
According to federal data, only 38% of U.S. health systems comply with the NIST Cybersecurity Framework, meaning the remaining 62% rely on legacy or partially secured technology.
The result? The healthcare sector now ranks second globally in vulnerability to ransomware attacks.
Operationally, the toll is equally severe. 83% of healthcare IT teams report that legacy technology disrupts daily operations, slowing down everything from patient intake to billing workflows.
How to Solve Problems Associated with Healthcare Legacy Systems?
Outdated systems are open doors for attackers. Modernization starts with visibility, patching, and planned replacement.
| 1. Identify and Audit Legacy Systems List every legacy platform and expose its weaknesses. You can’t defend what you can’t see. |
| 2. Patch and Prioritize Apply the latest updates and fund upgrades, especially for systems holding patient identity or intake data. |
| 3. Plan a Phase-Out Roadmap Build a 3-year plan to retire legacy tech in line with NIST CSF and HIPAA standards. |
| 4. Automate Patching Use automated tools to apply updates fast and consistently, thereby closing gaps before attackers find them. |
5. Healthcare Compliance Gaps
Federal mandates define the baseline for healthcare cybersecurity—but many still fall short. Despite HIPAA’s Security Rule, 41% of healthcare organizations maintain only partial safeguards.
Mandatory frameworks like HIPAA, HITECH, and NIST Cybersecurity Framework (CSF) are essential shields against ransomware, data breaches, and operational shutdowns. Full compliance isn’t paperwork; it’s protection.
| Compliance / Requirement | Definition | Key Requirements | Evidence of Compliance |
|---|---|---|---|
| HIPAA Security Rule (45 CFR Part 164 Subpart C) | Federal regulation that mandates safeguards to protect electronic Protected Health Information (ePHI). | Conduct documented risk analysis. Implement admin, physical, and technical safeguards. Maintain access controls and BAAs. |
Risk analysis reports, security policies, training logs, audit trails, and signed BAAs. |
| HITECH / HIPAA Breach Notification Rule | Requires timely notification to patients and HHS after any breach of unsecured PHI. | Report breaches ≥500 individuals to HHS within 60 days. Notify affected individuals. Keep breach logs. |
Breach logs, notification letters, OCR submission proof, incident response documentation. |
| NIST Cybersecurity Framework (CSF) + HICP (405d) | Federal best-practice framework outlining how to identify, protect, detect, respond, and recover from cyber threats. | Map existing controls to NIST CSF. Implement MFA, patching, segmentation, IR plan, and backups. |
NIST mapping sheet, patch reports, IR test results, backup verification records. |
Securing Digital Patient Intake: Why Certify Health Is the Trusted Choice for Unified Healthcare Management
Managing patients through third-party systems can introduce risk. Certify Health eliminates concerns with a secure, compliant, and unified healthcare management platform. Here’s how:
1. FaceCheck Biometric Authentication
Certify Health offers Facial recognition/verification, photo ID capture, and kiosk/mobile check-ins at every care stage. This prevents patient identity fraud and aligns with NIST recommendations for stronger authentication and protection against unauthorized disclosures.
2. Secure Digital Intake & Interoperability
With multichannel digital intake, e–Consents, insurance capture, and FHIR/HL7 integrations, Certify Health ensures encrypted, auditable, and tamper-proof data exchange. Its standards-based APIs make it future-proof against unsafe integrations, unlike custom or siloed systems.
Comprehensive audit trails across intake, billing, and RCM workflows enable quick incident detection and post-event investigation. Every action is logged for transparency and compliance.
4. Reduced Vendor Risk
Through EHR integrations (Epic, Cerner, Athena) and a centralized marketplace, Certify Health minimizes external vendor involvement. Fewer vendors mean a smaller attack surface and better Business Associate oversight, reducing third-party breach risks.
5. Real-Time Eligibility & Secure Payments
Integrated eligibility verification, Text-to-Pay, and RCM automation reduce manual data entry and human error, eliminating PHI leaks from spreadsheets or copy-paste workflows.
Conclusion
With HIPAA, NIST, and HL7/FHIR compliance at its core, Certify Health delivers end-to-end security, interoperability, and auditability. This protects both patient trust and provider operations.
Book a demo and see for yourself!